Executive Summary
In February 2024, a major healthcare company suffered a breach that exposed data for 110 million Americans. The cause? Basic security failures: no encryption, no two-factor authentication. The cost? $2.45 billion, a $22 million ransom, and irreparable damage to patient trust. [1]
This wasn’t a sophisticated attack. It was preventable. And it’s exactly why healthcare executives can no longer treat software security as an IT afterthought.
Healthcare organizations face a critical challenge: you need technology to compete and deliver modern care, but generic software solutions create dangerous compliance gaps. The average healthcare data breach now costs $7.42 million [2] with ransomware attacks on healthcare up 6% in 2024 [3] the question isn’t whether to invest in secure, compliant software. It’s whether you know how to build it right.
This guide walks you through what HIPAA compliance really means for your software, why generic solutions consistently fail healthcare organizations, and how custom healthcare software development solves these challenges while driving business growth.
The Real Cost of Getting Healthcare Software Wrong
Let’s start with what’s at stake.
When we talk about HIPAA compliance, most people think about fines. And yes, penalties range from $141 to over $2 million per violation. [4] But that’s not what keeps healthcare executives up at night.
The real costs are:
- Patient Trust: Once broken, it’s nearly impossible to rebuild. Patients who lose confidence in your ability to protect their data will seek care elsewhere. In healthcare, trust is your foundation.
- Operational Disruption: When a breach occurs, your systems may be locked for days or weeks. Staff can’t access records. Procedures get delayed. Patients are diverted to other facilities. Revenue stops, but expenses continue.
- Legal Liability: Class-action lawsuits from affected patients. Regulatory investigations. Potential criminal charges if negligence is proven. Legal costs alone can dwarf regulatory fines.
- Competitive Disadvantage: While you’re managing a crisis, competitors are winning your market share. Healthcare providers won’t refer patients to organizations with security problems. Payers won’t partner with risky entities.
- Long-Term Brand Damage: News of healthcare breaches spreads fast. Your organization’s name becomes associated with the breach, not your quality of care. This reputation damage persists for years.
Here’s what many healthcare leaders miss: most breaches don’t happen because of sophisticated hackers. They happen because software wasn’t built right in the first place.
Why Generic Software Consistently Fails Healthcare
You’ve probably experienced this: you implement a new software system, and within weeks, your team is frustrated. It doesn’t match your workflows. It can’t connect properly with your existing systems. And when you ask about specific security features HIPAA requires, you get vague answers or expensive customization quotes.
This happens because generic software is built for the broadest possible market. Healthcare is just one checkbox on their feature list.
Here’s why this approach fails:
- Security as an Add-On: Generic software developers build the core product first, then try to add security features later. But healthcare data security and compliance need to be foundational, built into every component from the start. You can’t retrofit true HIPAA compliance.
- One-Size-Fits-None Workflows: How you discharge patients, coordinate care, verify insurance, or schedule procedures is unique to your organization. Generic software forces you to abandon your optimized processes and adopt their rigid workflows, creating inefficiency and security gaps where workarounds become necessary. Automated clinical workflows should enhance your processes, not replace them with inferior alternatives.
- Integration Nightmares: Your organization uses multiple systems – EHRs, billing platforms, lab systems, imaging archives, and pharmacy networks. Generic software rarely integrates cleanly with all of these. Each poor integration creates a potential security vulnerability and compliance gap. Healthcare software interoperability is essential, not optional.
- Unclear Compliance Responsibility: When generic software vendors are asked to sign Business Associate Agreements legally required under HIPAA, many refuse or provide agreements with so many carve-outs that are essentially meaningless. Who’s actually responsible when something goes wrong? The answer is always: you are.
- The Hidden Costs of “Cheaper” Solutions: That attractive per-user pricing doesn’t include the customization fees, integration costs, compliance gaps you’ll need to address separately, workflow inefficiencies, and staff time spent working around limitations. By year two, the “affordable” option will cost more than custom development would have.
We’ve seen this pattern repeatedly: healthcare organizations choose generic software to save money, then spend two years and double the budget trying to make it work, before finally investing in custom development anyway.
Let’s talk about what actually works.
What HIPAA Compliance Really Means (Beyond the Buzzwords)
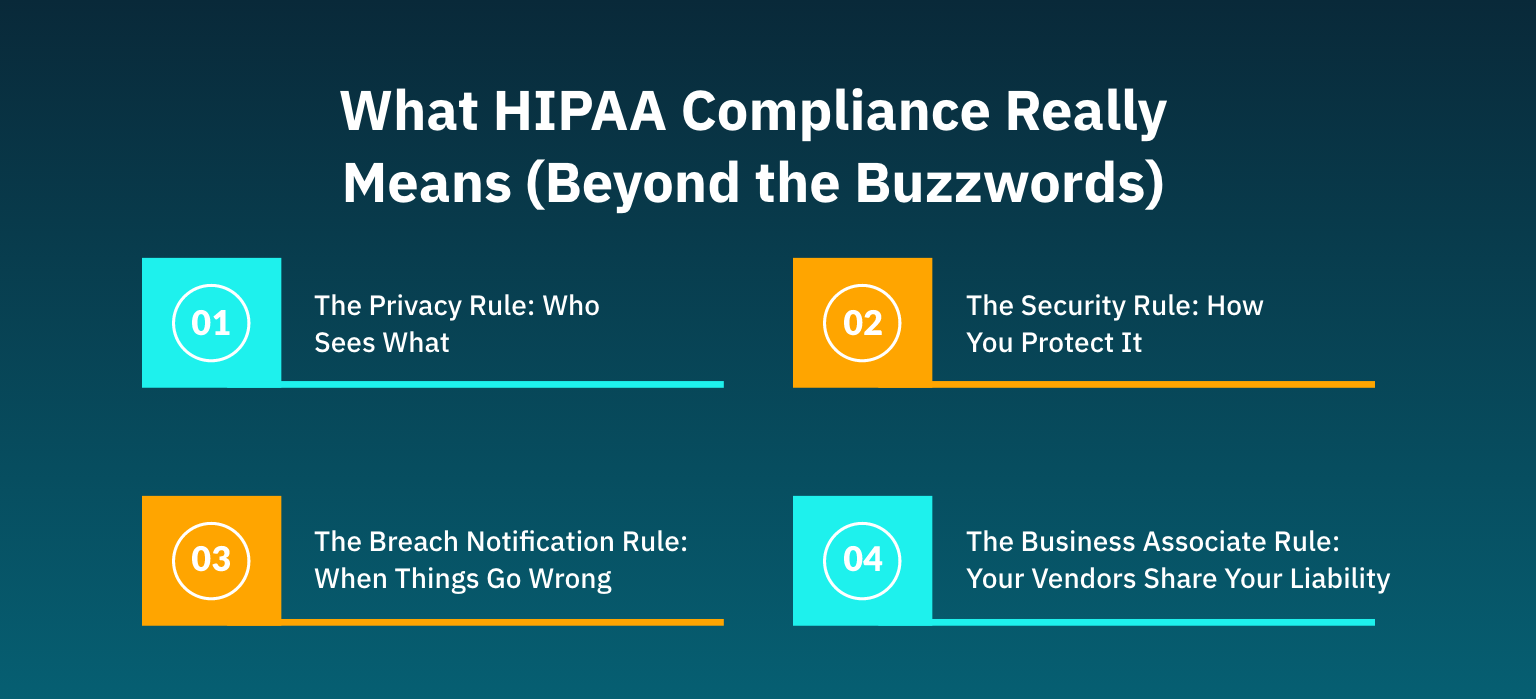
Before we discuss solutions, let’s clarify what you’re actually building toward. HIPAA compliance isn’t a single checklist; it’s a comprehensive framework with four key components:
1. The Privacy Rule: Who Sees What
This rule controls access to patient information. In practice, it means your software must:
- Limit data access based on job function (doctors see full records, billing staff only see payment information)
- Track and justify every access to patient data
- Allow patients to see who’s accessed their information
- Provide mechanisms for patients to request corrections or restrictions
The underlying principle: minimum necessary access. Users should only see the specific patient data they need for their specific task, nothing more.
2. The Security Rule: How You Protect It
This is where most software fails. The Security Rule requires three layers of protection:
- Technical safeguards: PHI data encryption, access controls, audit logs, secure transmission protocols, and automatic session timeouts. These HIPAA security features must work together seamlessly.
- Administrative safeguards: Risk assessments, staff training, incident response procedures, and designated compliance oversight.
- Physical safeguards: Controlled facility access, workstation security, and device management protocols.
Notice these aren’t just features you can buy; they require organizational processes and software designed to support them through secure medical data processing.
3. The Breach Notification Rule: When Things Go Wrong
Despite best efforts, breaches can happen. This rule requires you to:
- Notify affected individuals within 60 days
- Report to the Department of Health and Human Services
- Notify media if the breach affects 500+ people
- Maintain detailed documentation of the breach and response
Your software needs to support rapid breach assessment; you can’t comply with 60-day notification requirements if it takes you six months to figure out what data was accessed.
4. The Business Associate Rule: Your Vendors Share Your Liability
This is critical: if you work with any vendor that handles patient data on your behalf, they’re legally responsible for HIPAA compliance too. This includes:
- Healthcare software development companies
- Cloud hosting providers
- Analytics platforms
- Payment processors
- Any third-party integration
You need signed Business Associate Agreements (BAAs) with all of them. And if they violate HIPAA, you’re both liable.
This is why choosing your healthcare software development company matters so much. You’re not just buying software; you’re entering a compliance partnership.

The Five Core Requirements Your Healthcare Software Must Meet
Let us walk you through what actually makes software HIPAA-compliant. These aren’t optional features, they’re foundational requirements.
1. Data Protection Throughout Its Lifecycle
Patient data must be protected everywhere it exists through comprehensive patient data privacy AI mechanisms:
- At rest (stored in databases): Encrypted so if someone steals a hard drive or accesses your database, the data is unreadable without encryption keys.
- In transit (moving between systems): Encrypted connections for all data transfer when a doctor accesses records remotely, when systems exchange information, when patients use your portal.
- In use (being processed): Access controls ensuring only authorized users can decrypt and view data, even temporarily.
- In backup (disaster recovery): Encrypted backups stored securely with the same protections as production data.
Generic software often handles one or two of these well but creates gaps in others, especially in backups and data transmission to third-party integrations.
2. Granular Access Control (Who Sees What)
Different users need different access levels with proper encryption and access control:
- Physicians: Full access to their patients’ records
- Nurses: Access based on assigned patients
- Specialists: Access to relevant clinical information
- Administrative staff: Scheduling and demographic data only
- Billing: Financial information, limited clinical details
- External partners: Specific data only, time-limited access
Your software must enforce these permissions automatically and make them easy to manage as staff roles change. When an employee leaves or changes roles, their access should be updated immediately across all systems.
3. Complete Audit Trails
HIPAA requires logging every interaction with patient data:
- Who accessed it
- When they accessed it
- What they accessed
- What they did with it
- Where they accessed it from
These logs must be:
- Tamper-proof (users can’t delete their access history)
- Retained for at least six years
- Searchable for compliance audits
- Monitored for unusual patterns
Good audit systems also flag suspicious activity automatically: someone accessing hundreds of records they don’t normally work with, late-night access from unusual locations, or bulk data exports.
4. Secure Integration Architecture
Your healthcare software doesn’t exist in isolation. It connects with:
- Electronic Health Records (EHR/EMR software solutions)
- Laboratory information systems
- Imaging systems (PACS)
- Pharmacy networks
- Insurance verification services
- Telemedicine platforms and telemedicine AI solutions
- Medical devices and healthcare IoT integration
- Patient monitoring software systems
Each connection point must maintain the same security standards as your core system. One weak integration can compromise everything.
This is where custom healthcare software development becomes essential. Generic software provides standard APIs that often don’t match healthcare systems’ security requirements. Custom solutions build integrations that maintain compliance across the entire ecosystem.
5. Business Continuity and Disaster Recovery
HIPAA requires you to maintain access to patient data even during emergencies. Your software must include:
- Regular automated backups
- Geographic redundancy (data stored in multiple locations)
- Tested recovery procedures
- Maximum allowable downtime defined and documented
- Backup access methods if primary systems fail
When ransomware hits, you need to recover quickly without paying criminals. When natural disasters affect your primary data center, patient care can’t stop.
The AI Compliance Challenge: New Technology, New Risks
Healthcare organizations are excited about AI, and rightfully so. AI and ML in healthcare software offer tremendous potential for automating documentation, improving diagnostics, and personalizing care through clinical NLP models and AI–driven healthcare compliance. The healthcare AI market was valued at USD 26.57 billion in 2024 and is projected to reach USD 505.59 billion by 2033. [5]
But there’s a critical compliance issue many organizations discover too late: most popular AI tools can’t legally be used with patient data.
Why ChatGPT and Similar Tools Are HIPAA Violations
Here’s what happens: A well-meaning doctor asks ChatGPT to summarize patient notes. A billing specialist uses it to draft a letter to an insurance company that includes patient details. An administrator uploads appointment data to analyze patterns.
Each of these actions is a HIPAA violation.
Why? Because OpenAI (ChatGPT), Google (standard Gemini), and Anthropic (Claude) don’t sign Business Associate Agreements for their consumer services. Using these tools with any patient data, even a patient name combined with any health information, violates HIPAA. [6]
The risk isn’t just regulatory. AI systems can “hallucinate” and generate plausible but incorrect information. In one documented case, an AI chatbot provided medical advice that could have been fatal if followed. [7] In healthcare, incorrect AI outputs don’t just create liability; they endanger patients. Healthcare chatbot HIPAA compliance isn’t optional, it’s essential.
How to Use AI Compliantly in Healthcare
You have three paths forward for implementing healthcare AI security:
Option 1: Self-Hosted HIPAA LLM Models
Deploy open-source AI models on your own servers. Patient data never leaves your secure environment. Organizations like Stanford Medicine have done this successfully with their “Secure GPT” program. [8]
Best for: Large health systems with dedicated technical teams and infrastructure budgets.
Option 2: Enterprise Cloud AI Services
Use healthcare–specific AI from providers like Microsoft Azure, AWS, or Google Cloud. These come with Business Associate Agreements and proper security controls, but only in their enterprise healthcare configurations, not standard offerings.
Best for: Organizations want powerful AI capabilities without managing infrastructure.
Option 3: Healthcare-Specialized AI Vendors
Work with companies that specifically serve healthcare and handle all compliance requirements through HIPAA-compliant LLM solutions.
Best for: Organizations prioritizing fast deployment and guaranteed compliance over customization.
Non-Negotiable AI Safeguards
Regardless of which path you choose:
- Get patient consent before AI processes their data; clear documentation explaining what data is used and why.
- Remove identifiers when possible before AI processing, reducing risk if something goes wrong.
- Maintain comprehensive logs of all AI interactions with patient data; who used it, when, what data was involved.
- Require human review of all AI outputs before they affect patient care; AI assists clinicians, never replaces them.
- Verify vendor compliance thoroughly; signed BAAs, regular security audits, incident response procedures documented.
How Custom Healthcare Software Solves These Challenges
Now that you understand what HIPAA compliance requires and why generic software falls short, let’s discuss how custom healthcare software solutions addresses these challenges.
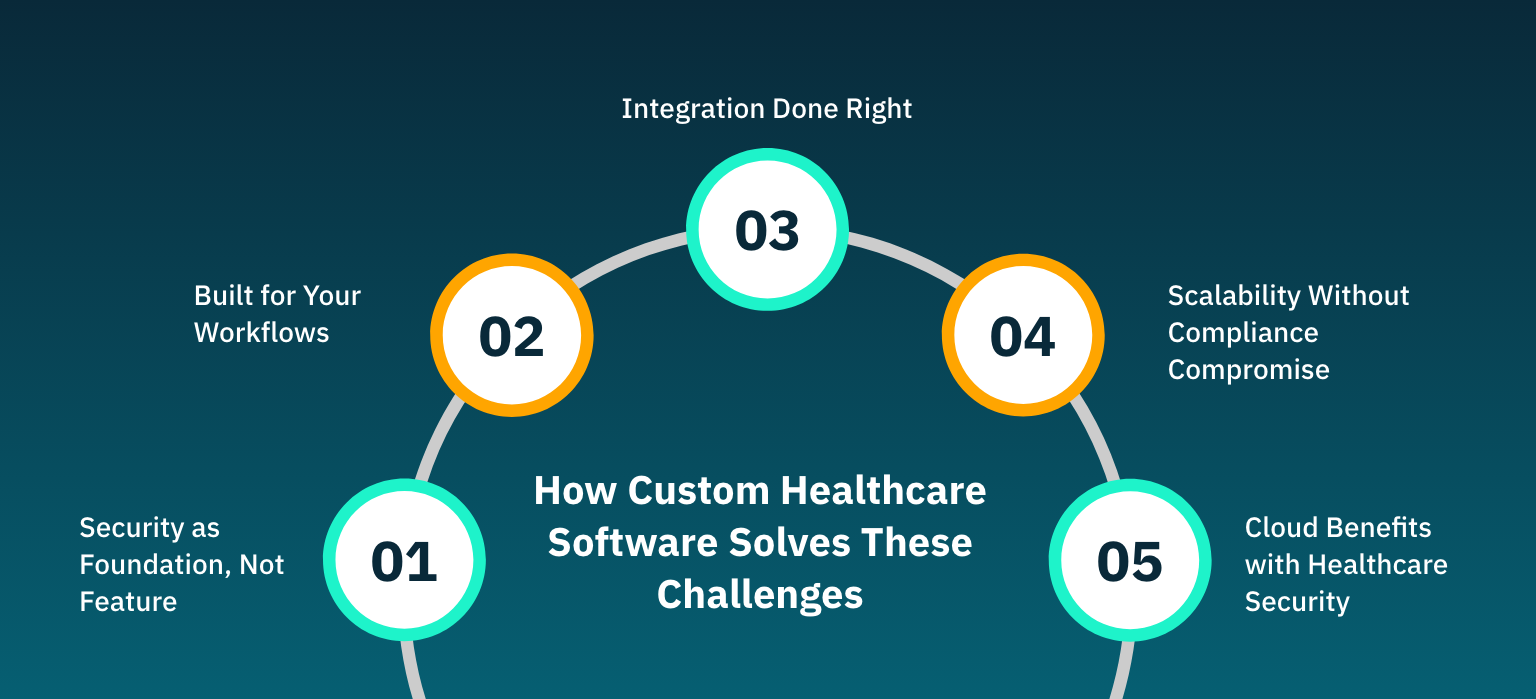
Security as Foundation, Not Feature
Custom healthcare software development starts with compliance as a core requirement, not an afterthought. Here’s the difference:
Generic Software Approach: Build the product → Add security features → Try to retrofit HIPAA compliance → Discover gaps → Create workarounds → Hope for the best
Custom Development Approach: Define compliance requirements → Design security architecture → Build features within secure framework → Test against HIPAA standards → Deploy with compliance embedded → Maintain ongoing
The result? No security gaps, no workarounds, no hoping. Just software designed to be compliant from day one.
Built for Your Workflows
When we develop HIPAA-compliant healthcare software development solutions, we start by understanding how your organization actually works:
- How do you currently discharge patients?
- What information do different staff members need access to?
- Which systems need to communicate with each other?
- Where are the bottlenecks in your current processes?
- What makes your organization different from competitors?
Then we build software that supports these workflows while maintaining security. Your staff doesn’t need to change how they work; the software adapts to them with automated clinical workflows that enhance efficiency without compromising compliance.
Integration Done Right
Healthcare IT environments are complex. You might have:
- An EHR/EMR software solutions system from one vendor
- Billing software from another
- Lab systems, imaging archives, pharmacy networks
- Specialty applications for specific departments
- Medical devices generating data through healthcare IoT integration
- Patient monitoring software for real-time care
- Voice-assisted healthcare apps for documentation
Custom development creates secure bridges between all these systems. Each integration is designed with:
- Proper authentication and authorization
- Encrypted data transfer through secure medical data processing
- Audit logging of all exchanges
- Error handling that doesn’t expose patient data
- Performance monitoring
When everything connects properly through healthcare software interoperability, you gain efficiency without sacrificing security.
Scalability Without Compliance Compromise
As your organization grows, your needs change. New locations, new services, new partnerships, new regulations.
Generic software forces you to buy bigger packages or switch platforms entirely. Custom healthcare software solutions scale with you by adding capacity, features, or locations without rebuilding from scratch.
More importantly, the compliance foundation stays solid as you grow. New features inherit the same security architecture. New integrations follow the same secure patterns. Scaling doesn’t mean starting over with compliance.
Cloud Benefits with Healthcare Security
Many healthcare organizations are moving to cloud-based healthcare solutions for good reasons: it can reduce IT costs, provide better disaster recovery, and offer access to advanced technologies.
But not all cloud implementations are created equal. Custom development ensures:
- Proper Configuration: Cloud platforms are flexible, which means they can be misconfigured. We set up healthcare cloud environments with security built in.
- Right Vendor Selection: Not all cloud providers offer healthcare-appropriate services. We work with providers who sign Business Associate Agreements and have healthcare-specific security capabilities.
- Hybrid Architecture When Needed: Some organizations need certain data on-premises while leveraging cloud for other services. Custom solutions create secure hybrid environments.
- Cost Management: Cloud costs can spiral without proper architecture. We design solutions that provide the benefits of cloud while controlling expenses.
The key is having partners who understand both healthcare compliance and cloud technology, not just one or the other.
Real-World Results: Custom Solutions in Action
Let us show you how this works in practice with two examples from organizations that faced specific challenges.
Case Study: MaxMRJ – Solving the Discharge Coordination Problem
The Challenge
Hospitals were losing money on inefficient patient discharges. Staff used spreadsheets, emails, and phone calls to coordinate with skilled nursing facilities and hospice providers. This created delays (keeping patients in expensive hospital beds longer), frequent miscommunication, administrative burden, and compliance risks from unsecured PHI sharing.
Why Generic Software Couldn’t Solve It
Available discharge planning tools didn’t integrate with both hospital EMRs and skilled nursing facility systems. They couldn’t handle the complex referral networks each hospital had built. The security model didn’t support the multi-organizational data sharing required. Pricing models made them too expensive for the smaller care facilities that needed access.
The Custom Solution
Matellio built MaxMRJ specifically for this use case:
- Direct integration with hospital EMR systems to pull patient data securely
- Automated matching of patients with appropriate care facilities based on needs and availability
- Secure communication platform replacing emails and phone calls
- Role-based access so different facility types saw only relevant information
- Real-time tracking of the entire discharge process
- Comprehensive audit trails for compliance
Business Results:
- Significantly faster discharge processing (reducing hospital costs)
- Eliminated unsecured PHI sharing via email
- Improved coordination between hospitals and care facilities
- Better visibility into referral network performance
- Scalable platform that could grow with additional facilities
This demonstrates a key principle: when you build software for a specific healthcare challenge, you can solve it completely while maintaining compliance; something generic software can never do
Case Study: 1+1 Cares—Scaling Caregiver Services Securely
The Challenge
A caregiver referral agency was managing everything manually through Excel: caregiver credentials, background checks, client matching, payments, scheduling. This created 5-6 day delays in verifying new caregivers (limiting growth), high error rates in matching, manual invoice processing consuming staff time, and difficulty maintaining compliance with personal data scattered across spreadsheets.
Why Generic Software Couldn’t Solve It
Available healthcare staffing platforms were designed for hospitals, not caregiver agencies. They didn’t handle the specific workflow of matching caregivers with home care clients. They couldn’t integrate with the background check services this agency used. The pricing model was based on per-employee fees that didn’t work for this business model.
The Custom Solution
Matellio developed a mobile platform specifically for caregiver referral operations:
- Integration with Checkr for automated background verification
- Smart matching algorithm considering location, credentials, availability, and client needs
- Secure messaging, voice, and video capabilities via Twilio
- Automated billing and commission calculations
- Document management for credentials and certifications
- All with HIPAA-compliant security for personal health informatio
Business Results:
- 98% reduction in caregiver verification time (5-6 days to minutes)
- Able to scale operations rapidly with automated processes
- Higher client satisfaction from better caregiver matching
- Eliminated manual processing errors
- Secure handling of sensitive data throughout
This example shows another key principle: custom solutions enable business models that generic software can’t support, while maintaining the security and compliance healthcare requires.
The Pattern You Should Notice
Both cases share important characteristics:
- Specific business problems that generic software couldn’t solve
- Custom solutions designed around actual workflows
- Integration with existing systems done securely
- Compliance built into the core, not added later
- Measurable business results—efficiency, cost savings, growth enablement
- Scalability to support future growth
This is what happens when you work with a healthcare software development company that understands both the technology and the business challenges you face.
What to Look for in a Healthcare Software Development Partner
1. Compliance-First Thinking (Not Compliance-Later Fixing)
Ask potential partners: “When in your development process do you address HIPAA compliance?”
Red flag answer: “We build the features first, then add security and compliance.”
What you want to hear: “We start every project by defining compliance requirements and building them into the architecture from day one.”
2. Healthcare Domain Experience You Can Verify
Look for partners with:
- Specific healthcare project experience: Ask to see case studies from healthcare organizations similar to yours. What challenges did they solve? What were the measurable results?
- Understanding of healthcare workflows: Can they discuss how different clinical roles interact with systems? Do they understand the unique requirements of hospitals versus clinics versus care coordination services?
- Integration expertise: Have they connected systems with major EHR platforms (Epic, Cerner, Meditech)? Can they work with HL7, FHIR, and other healthcare data standards?
- Regulatory knowledge: Do they understand HIPAA, HITECH, state privacy laws, and how these intersect? Can they explain the Business Associate relationship clearly?
3. Full-Spectrum Development Capabilities
Healthcare software projects typically require:
- Strategic planning: Understanding your business challenge, not just technical requirements
- Architecture design: Creating systems that are secure, scalable, and maintainable
- Development: Writing code that follows healthcare security best practices
- Integration: Connecting with your existing healthcare ecosystem
- Testing: Both functional testing and security testing
- Deployment: Secure implementation in your environment
- Ongoing support: Continuous monitoring, updates, and compliance maintenance
Partners who can only handle one or two of these will leave gaps you’ll need to fill with other vendors, thus creating coordination challenges and potential security issues.
4. Technology Breadth Across Healthcare Needs
Your current project might be a telemedicine platform. But next year you might need patient monitoring, AI-powered analytics, or IoT device integration. Partners with experience across healthcare technology domains can grow with you:
- Telemedicine app development
- EHR/EMR software solutions
- Healthcare CRM software development
- Medical management software development
- Patient monitoring software
- Healthcare IoT integration
- AI and ML in healthcare software (done compliantly)
- Voice-assisted healthcare apps
- Blockchain for healthcare data management
Breadth matters because healthcare IT is interconnected. The partner who builds your telemedicine platform should understand how it will need to integrate with your EHR system and patient portal.
5. Transparency About Process and Pricing
Be wary of partners who:
- Can’t clearly explain their development methodology
- Provide vague estimates without understanding your requirements
- Promise unrealistic timelines
- Avoid discussing how they handle compliance documentation
- Won’t connect you with past healthcare clients
Good partners are transparent about:
- How they’ll approach your project
- What timeline is realistic given your requirements
- What your total investment will include
- What you’ll receive at each project stage
- How they’ll document compliance for audits
6. Long-Term Partnership Orientation
HIPAA-compliant software isn’t build-it-and-forget-it. Regulations evolve. Threats change. Your business grows. You need a partner who thinks beyond project completion:
- Do they offer ongoing security monitoring?
- How do they handle updates when HIPAA requirements change?
- Can they scale the solution as you grow?
- Do they provide compliance documentation for audits?
- Are they responsive when issues arise?
How Matellio Approaches Healthcare Software Development
1. We Start With Your Business Challenge
Most software projects start with a requirements document. We start with a business conversation:
- What problem are you trying to solve?
- Why haven’t existing solutions worked?
- What would success look like?
- How does this fit into your broader strategy?
Only after understanding the business context do we discuss technical requirements. This ensures we’re building software that solves your actual problem, not just implementing a features list.
2. Compliance Is Built Into Our Foundation
We’ve developed custom healthcare software solutions for hospitals, clinics, healthcare technology companies, and care coordination services. Every project starts with:
- Compliance requirements mapping: What regulations apply to your specific situation? What data will you handle? What are your documentation requirements?
- Security architecture design: How will we protect data at rest, in transit, in use, and in backup? What access controls are needed? How will we create audit trails?
- Business Associate Agreements: We sign BAAs as part of our engagement, making our compliance responsibility legally clear.
- Documentation for audits: Throughout development, we create the documentation you’ll need for compliance audits.
3. Our Healthcare Technology Expertise
We’ve built solutions across the healthcare technology spectrum, ranging from Telemedicine apps, medical management software, EHR/EMR software solutions integration, Healthcare CRM software, Patient monitoring software, Healthcare IoT integration, AI and ML based healthcare software, Voice-assisted healthcare apps, and more.
4. We’re healthcare specialists, not generalists
We focus on healthcare because it requires specialized knowledge. We don’t treat HIPAA as just another compliance framework; we understand the clinical context behind the regulations.
5. We think long-term
We’re not just building software; we’re creating a foundation for your digital health strategy that can grow with you.
6. We communicate clearly
Healthcare compliance is complex, but our explanations aren’t. We translate technical requirements into business language.
7. We take responsibility
When we sign a Business Associate Agreement, we mean it. Your compliance is our compliance.
Making Your Decision: Next Steps
You’re now equipped with the knowledge to make an informed decision about healthcare software development. The question now is: what’s your next step?
If you’re considering new healthcare software; whether it’s a telemedicine platform, patient management system, care coordination tool, or any other healthcare application, we should talk.
Not a sales pitch. A consultation. We’ll discuss:
- Your specific challenges and goals
- Whether custom development makes sense for your situation
- What a realistic timeline and investment would look like
- How we’d approach your unique requirements
Even if you’re just starting to explore options, a conversation now can help you avoid expensive mistakes later.
Key Takeaways
- Healthcare breaches cost an average $9.77 million with ransomware attacks up 65% in 2024
- Generic software treats healthcare as one segment, creating inevitable compliance gaps
- HIPAA has four components: Privacy Rule, Security Rule, Breach Notification, Business Associate requirements
- Five core technical requirements: data protection, access control, audit trails, secure integration, business continuity
- Popular AI tools like ChatGPT cannot be used with patient data. Use self-hosted models, enterprise cloud AI, or specialized vendors
- Custom healthcare software development builds compliance into the foundation, not as an afterthought
- Cloud-based healthcare solutions can reduce costs with proper security configuration
- Your software vendor shares HIPAA liability through Business Associate Agreements
- Healthcare software interoperability is essential; integration is where security often breaks
- Choose partners with compliance-first thinking and verified healthcare project experience
FAQ’s
Three compliant approaches exist:
- Self-Hosted Models: Deploy open-source AI on your servers. Patient data never leaves your environment. Stanford’s “Secure GPT” demonstrates this. [8] Requires technical expertise and resources. Best for large health systems.
- Enterprise Cloud AI: Use Azure OpenAI, AWS Bedrock, or Google Cloud with signed Business Associate Agreements. Professional management without infrastructure burden. Best for organizations wanting enterprise AI capabilities.
- Healthcare AI Vendors: Specialized companies provide HIPAA-compliant solutions handling all compliance. Fastest deployment but higher costs. Best for rapid implementation.
All require: data encryption, strict access controls, comprehensive audit logs, signed Business Associate Agreements, and human review of AI outputs.
Securing patient data with AI requires multiple layers of protection:
- Before Processing: Obtain explicit patient consent. De-identify data when possible, though proper de-identification is complex.
- During Operations: Implement role-based access controls. Verify signed Business Associate Agreements. Keep comprehensive logs (HIPAA requires six-year retention).
- After Outputs: Require clinical staff review before AI affects patient care. Never allow autonomous AI decisions. Establish escalation procedures for incorrect outputs.
- Ongoing: Monitor AI performance as models drift. Review usage patterns regularly. Stay current with FDA guidance and state AI laws. Remember you’re legally responsible for vendor compliance.
No. This is one of the most critical compliance issues healthcare organizations face with AI.
Standard ChatGPT, Google Gemini, and similar public AI tools cannot legally be used with any patient data. Here’s why: OpenAI, Google, and Anthropic do not sign Business Associate Agreements for their consumer-tier services. Under HIPAA, using these tools with PHI, even seemingly harmless uses, constitutes a violation.
Self-hosted models ensure compliance through data sovereignty; patient information never leaves your environment.
Required Controls:
- Technical: Encrypt data at rest and in transit, role-based access controls, complete audit logging, network segmentation, regular security updates
- Administrative: Document security policies, train staff, establish incident response plans, conduct regular risk assessments
- Operational: Test disaster recovery regularly, document model selection process, maintain performance monitoring, require human review of outputs
Advantage: Complete control without third-party dependencies.
Challenge: Requires substantial AI engineering and healthcare security expertise. Stanford succeeded [8] but dedicated significant resources.
Assess your team’s expertise before pursuing or plan to hire specialized talent.
Key Risks:
- Data exposure through logs, errors, or outputs
- AI hallucinations generating incorrect but authoritative-sounding information [7]
- Training data revealing memorized patient information
- Vendor liability (you’re responsible for their violations)
- Model drift compromising compliance over time
Required Compliance:
- Maintain signed Business Associate Agreements with AI vendors
- Conduct AI-specific risk assessments
- Implement audit logging with six-year retention
- Establish AI-specific incident response procedures
- Train staff on AI limitations and appropriate use
- Document AI governance (selection, validation, monitoring, oversight)
- Obtain explicit patient consent
- Stay current with FDA guidance, EU AI Act, and state regulations
Bottom Line: Build innovation and compliance together from the foundation, not as an afterthought.
References
1. UnitedHealth Ransomware Attack Exposes 190M Users’ Personal & Healthcare Data
2. Average Cost of a Healthcare Data Breach Falls to $7.42 Million
3. The State of Ransomware in Healthcare 2024 – Sophos News
4. HIPAA Violation Fines – Updated for 2025
5.AI In Healthcare Market Size & Share | Industry Report, 2033
6. HIPAA-Compliant AI Alternatives. https://www.hipaajournal.com/when-ai-technology-and-hipaa-collide/
7. Doctors’ Study Finds 5-13% of Chatbot Medical Advice Is Dangerous or Unsafe – Unite.AI